|
Home
Home
Introduction
Historical Background
GSM
EDGE
WCDMA
UMTS
The Future
Final Thoughts
Blueadmiral.com
|
Protocols
Figure 7 shows the
architecture of protocols used within the GSM system, with signalling
protocols, interfaces as well as the entities already shown in Figure 5.
Again the main area of focus is in the Um interface, this is because the
other interfaces occur between entities in a fixed network. The physical
layer, Layer 1 handles all the radio specific functions. This layer
includes the creation of bursts according to the five different formats,
the multiplexing of bursts into TDMA frames, synchronisation with the
BTS, detection of the idle channels and the measurement of the channel
quality on the downlink. At Um, the physical layer uses GSMK (Gaussian
Shift Minimum Keying) for the digital modulation and performs
encryption/decryption of data This means that encryption is not
performed end-to-end, but only between MS and BTS over the air
interface.
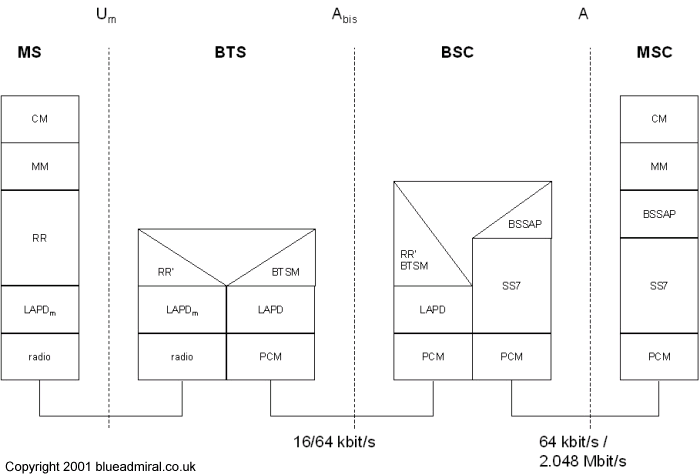
Figure 7 Protocol
Architecture for signalling
The synchronisation also includes the correction of the individual path
delay between the MS and the BTS, all MSs within a cell can use the same
BTS and hence must be synchronised to the BTS. This is due to the fact
that the BTS generated the time-structure of the frames and slots etc.
This can be problematic since in this context there are different RTTs
(Round Trip Time). An MS that is close to the BTS has a very short RTT
whereas an MS that is 35 km away has a RTT of around 0.23 ms.. If the MS
35 km away used the slot structure without correction, a large guard
spaces would be required as 0.23 ms. are already 40% of the 0.577 ms
available for each time slot. (Wray Castle, GSM Appreciation, 1998.).
Therefore the BTS sends the current RTT to MS, which then adjusts its
access time so that all bursts reach the BTS within their limits. This
mechanism ensures that the guard space is reduced to only 30.5 ms or 5%.
See Figure 7. This means the adjustment of the access is controlled via
the variable timing advance, where a burst can be shifted up to 63 bit
times earlier, with the resulting bits having a duration of 3.69 ms,
thus will result in the 0.23 ms needed.
The physical layer has several main tasks that comprise the channel
coding, error detection/correction; this is directly combined with the
coding mechanisms. FEC (Forward Error Correction) is used extensively in
the coding channel, FEC adds redundancy to the user data, thus allowing
for the detection and correction of selected errors. The power of the
FEC scheme depends on the amount of redundancy, coding algorithm, and
any further interleaving of data to minimise the effects of burst
errors. Whatsmore the FEC is the reason that error detection/correction
occurs in the physical layer. This differs to the ISO/OSI reference
model where it occurs in layer two. The GSM physical layer tries to
correct errors, however it does not deliver erroneous data to the higher
layers.
GSM logical channels use different coding schemes with different
correction capabilities, for example speech channels need the additional
coding of voice data after analogue to digital conversion. This is in
order to reach a data rate of 22.8 kbit/s (using the 13 kbit/s from the
voice codec plus redundancy, CRC bits, and interleaving (Goodman, 1997).
When GSM was envisaged it was assumed that voice would be the main
service so the physical also contains special functions, for instance
VAD (Voice Activity Detection), which transmits voice data only when
there is a voice signal. In the duration between voice activity, the
physical layer generates a comfort noise to fake a connection, however
no actual transmission takes place.
All the interleaving in the voice channel is to minimise interference
due to burst errors and the recurrence pattern of a logical channel
generates a delay for transmission, although this delay is only about 60
ms for TCH/FS and about 100 ms for TCH/F9.6. These times have to be
added to the transmission delay if the BTS is communicating with an MS
rather than a standard fixed station (for example a stationary computer
etc.) and this in turn may influence the performance of any of higher
layer protocols, e.g.. for computer data transmission.
Signalling between the entities within the GSM network requires the use
of the higher layers (see Figure 7). For this, the LAPDm (Link Access
Procedure for the D-Channel) protocol has been defined at the Um
interface for layer two. As the name already implies, it has been
derived from link access procedure for the D-Channel (LAPD) in the ISDN
system, which is a version of HDLC (Goodman, 1997), LAPDm is a
lightweight version of LAPD, in that it does not require synchronisation
flags or check summing for error detection, these are not needed as
these functions are already performed in the physical layer of the GSM
network. LAPDm, however offers reliable data transfer over connections,
re-sequencing of data frames and flow control (ETSI, 1993, ETS 300 937),
(ETSI, 1999) TS 100 938. Due to the fact that there is no buffering
between layer one and two, the LAPDm has to obey the frame structures,
recurrence patterns etc defined for the reassembly of data and
acknowledged/unacknowledged data transfer.
Layer three in the GSM network is made up of several sublayers as shown
in Figure 7, the lowest sublayer is the RR (Radio Resource Management).
Only part of this layer the RR', is implemented in the BTS, the
remainder of the RR is situated in the BSC. The BSC via the BTSM (Base
Transceiver Station Management) are responsible for the functions of the
RR'. The RR' has the function of setting up, maintenance and release of
the radio channels. Also the RR' has direct access to the physical layer
for radio information and offers a reliable connection to next higher
layer.
The physical layer has
several main tasks that comprise the channel coding, error
detection/correction; this is directly combined with the coding
mechanisms. FEC (Forward Error Correction) is used extensively in the
coding channel, FEC adds redundancy to the user data, thus allowing for
the detection and correction of selected errors. The power of the FEC
scheme depends on the amount of redundancy, coding algorithm, and any
further interleaving of data to minimise the effects of burst errors.
Whatsmore the FEC is the reason that error detection/correction occurs
in the physical layer. This differs to the ISO/OSI reference model where
it occurs in layer two. The GSM physical layer tries to correct errors,
however it does not deliver erroneous data to the higher layers.
GSM logical channels use different coding schemes with different
correction capabilities, for example speech channels need the additional
coding of voice data after analogue to digital conversion. This is in
order to reach a data rate of 22.8 kbit/s (using the 13 kbit/s from the
voice codec plus redundancy, CRC bits, and interleaving (Goodman, 1997).
When GSM was envisaged it was assumed that voice would be the main
service so the physical also contains special functions, for instance
VAD (Voice Activity Detection), which transmits voice data only when
there is a voice signal. In the duration between voice activity, the
physical layer generates a comfort noise to fake a connection, however
no actual transmission takes place.
All the interleaving in the voice channel is to minimise interference
due to burst errors and the recurrence pattern of a logical channel
generates a delay for transmission, although this delay is only about 60
ms for TCH/FS and about 100 ms for TCH/F9.6. These times have to be
added to the transmission delay if the BTS is communicating with an MS
rather than a standard fixed station (for example a stationary computer
etc.) and this in turn may influence the performance of any of higher
layer protocols, e.g.. for computer data transmission.
Signalling between the
entities within the GSM network requires the use of the higher layers
(see Figure 7). For this, the LAPDm (Link Access Procedure for the
D-Channel) protocol has been defined at the Um interface for layer two.
As the name already implies, it has been derived from link access
procedure for the D-Channel (LAPD) in the ISDN system, which is a
version of HDLC (Goodman, 1997), LAPDm is a lightweight version of LAPD,
in that it does not require synchronisation flags or check summing for
error detection, these are not needed as these functions are already
performed in the physical layer of the GSM network. LAPDm, however
offers reliable data transfer over connections, re-sequencing of data
frames and flow control (ETSI, 1993, ETS 300 937), (ETSI, 1999) TS 100
938. Due to the fact that there is no buffering between layer one and
two, the LAPDm has to obey the frame structures, recurrence patterns etc
defined for the reassembly of data and acknowledged/unacknowledged data
transfer.
Layer three in the GSM
network is made up of several sublayers as shown in Figure 7, the lowest
sublayer is the RR (Radio Resource Management). Only part of this layer
the RR', is implemented in the BTS, the remainder of the RR is situated
in the BSC. The BSC via the BTSM (Base Transceiver Station Management)
are responsible for the functions of the RR'. The RR' has the function
of setting up, maintenance and release of the radio channels. Also the
RR' has direct access to the physical layer for radio information and
offers a reliable connection to next higher layer. |

